2D Sine Logistic Modulation Map
Introduction
Because of the excellent properties of unpredictability, ergodicity and sensitivity to their parameters and initial values, chaotic maps are widely used in security applications. In this paper, we introduce a new two-dimensional Sine Logistic modulation map (2D-SLMM) which is derived from the Logistic and Sine maps. Compared with existing chaotic maps, it has the wider chaotic range, better ergodicity, hyperchaotic property and relatively low implementation cost. To investigate its applications, we propose a chaotic magic transform (CMT) to efficiently change the image pixel positions. Combining 2D-SLMM with CMT, we further introduce a new image encryption algorithm. Simulation results and security analysis demonstrate that the proposed algorithm is able to protect images with low time complexity and a high security level as well as}to resist various attacks.
2D Sine Logistic modulation map
2D Sine-Logistic modulation map (2D-SLMM) is defined as
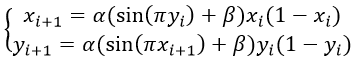 |
Where α and β are control parameters. α∈[0,1] and β∈[0,3].
Figure 1 shows the bifurcation diagram of 2D-SLMM.
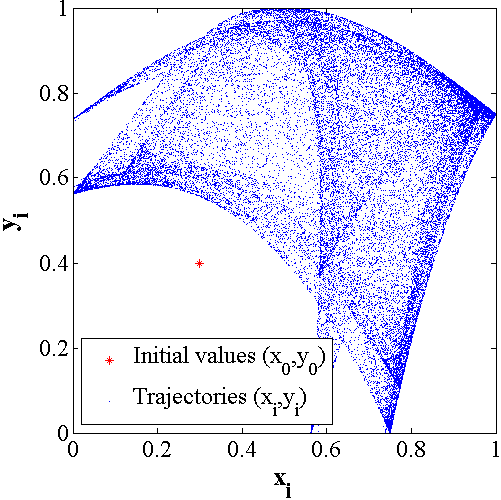 |
| Figure 1. The bifurcation diagram of 2D-SLMM. |
New CMT-based image encryption algorithm (CMT-IEA)
Figure 2 shows the flowchart of CMT-IEA. The plaintext image P is the original image and the ciphertext image C is the encrypted image. The security key is used to produce initial values and parameters of 2D-SLMM. CMT is to achieve the confusion property by randomly shuffling all pixel positions. The pixel substitution operations are to achieve the diffusion property by randomly changing all pixel values. To obtain random-like encryption results while avoiding the cases that 2D-SLMM may lose its chaotic behaviors in some parameter settings, the proposed CMT-IEA uses two rounds of CMT and pixel substitution operations. The decryption process simply reverses the encryption operations of CMT-IEA.
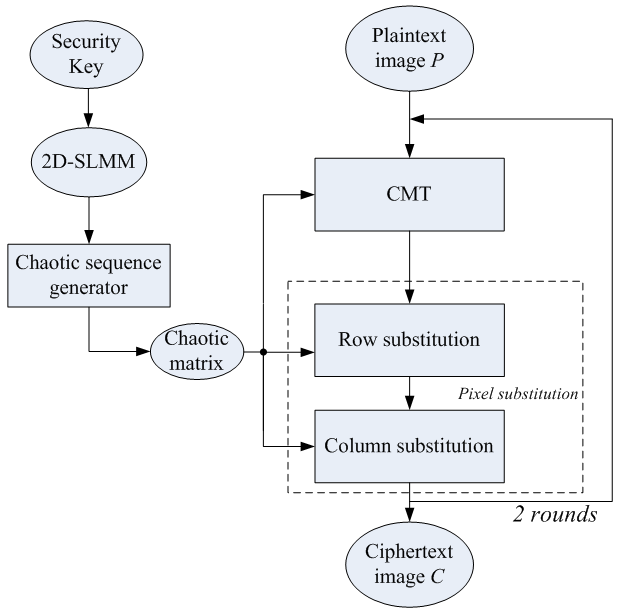 |
| Figure 2. The flowchart of the proposed CMT-IEA. |